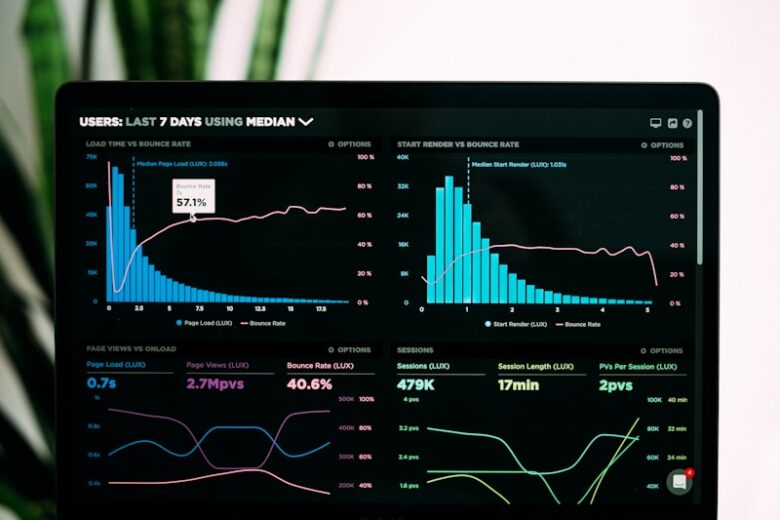
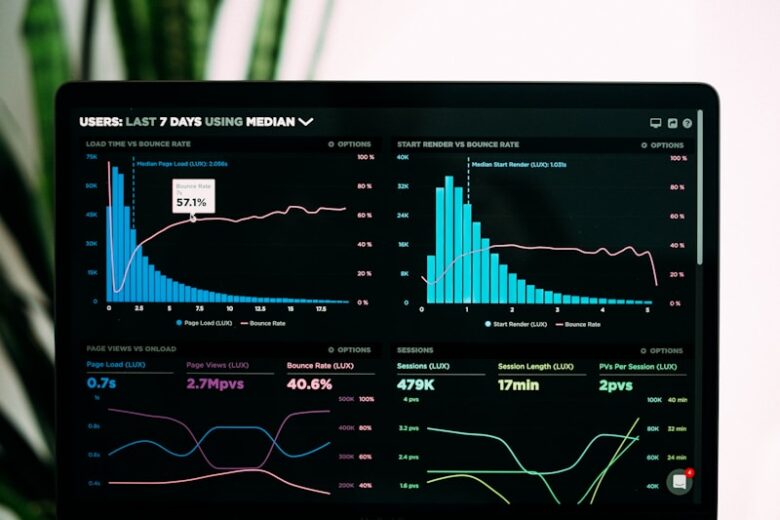
Edge computing brings computation closer to data sources, reducing latency and bandwidth usage. However, this distributed architecture introduces unique security challenges that require specialized approaches to protect edge devices and data. Edge Security Challenges Physical Security: Devices in uncontrolled environments Limited Resources: Constrained compute for security controls Network Exposure: Increased …
Chaos Engineering for Resilience Testing: A Practical Guide
Chaos Engineering is the discipline of experimenting on distributed systems to build confidence in their ability to withstand turbulent conditions. By proactively injecting failures, teams discover weaknesses before they cause outages. Chaos Engineering Principles Build Hypothesis: Define expected system behavior Vary Real-World Events: Simulate realistic failures Run in Production: Test …
Infrastructure Observability and Distributed Tracing Implementation
Observability goes beyond traditional monitoring by providing deep insights into system behavior through metrics, logs, and traces. Distributed tracing is essential for understanding request flows across microservices architectures. Three Pillars of Observability Metrics: Numerical measurements over time (latency, error rates) Logs: Discrete events with context Traces: Request journey across services …
Platform Engineering and Internal Developer Platforms (IDP)
Platform Engineering focuses on building and maintaining Internal Developer Platforms (IDPs) that enable self-service capabilities for development teams. By abstracting infrastructure complexity, platform teams accelerate delivery while maintaining governance and security. What is an Internal Developer Platform? An IDP is a layer on top of existing infrastructure that provides developers …
Immutable Infrastructure and Configuration Drift Prevention
Immutable infrastructure is a paradigm where servers are never modified after deployment. Instead of patching existing systems, you replace them entirely with new instances built from a common image. This approach eliminates configuration drift and improves reliability. Benefits of Immutable Infrastructure Consistency: Every deployment is identical Reliability: No configuration drift …
Service Mesh Security and Zero Trust Networking with Istio
Service meshes like Istio provide a dedicated infrastructure layer for handling service-to-service communication. They enable zero trust networking by implementing mutual TLS, fine-grained access control, and observability without changing application code. Zero Trust Principles in Service Mesh Never Trust, Always Verify: Authenticate every request Least Privilege Access: Explicit authorization policies …
Cloud Cost Optimization and FinOps Strategies for Engineering Teams
FinOps brings financial accountability to cloud spending by combining systems, best practices, and culture. This guide covers practical strategies for optimizing cloud costs while maintaining performance and reliability. FinOps Framework Phases Inform: Visibility into cloud spending and allocation Optimize: Identify and implement cost reduction opportunities Operate: Continuous governance and improvement …
Building Systems for Observability-First Operations: A Practical Guide
Hey there! Ever felt like you’re flying blind when something goes wrong with your systems? You’re not alone. I’ve been there. Many times! That’s why I’m so passionate about observability. It’s not just a buzzword; it’s a way of building systems that are easier to understand, troubleshoot, and improve. In …
The Cloud’s Role in Building a Sustainable Future
Hey there! Ever wondered how the technology we use every day is impacting the planet? We’re all thinking about it, right? From recycling our plastic bottles to choosing electric cars, we’re trying to be greener. But what about the digital world? Well, that’s where the cloud comes in. And let …
Understanding DSPM: Your Guide to Data Security Posture Management
Hey there! Ever feel like your data is a precious treasure, but you’re not quite sure how well-protected it is? That’s where Data Security Posture Management, or DSPM, comes in. Think of it as your personal data bodyguard. I’ve been diving deep into this topic lately, and let me tell …
How to Protect Your AI Models and Training Data: A Beginner’s Guide
Hey there! Ever wonder how those super-smart AI programs actually work? They’re amazing, right? But have you stopped to think about how we keep them safe? Because let’s face it, in this digital world, everything needs protection. And that includes the brains behind our AI – the AI models …
What Developers Need to Know About Sovereign Cloud
Hey there, fellow developers! Ever heard the buzz around “sovereign cloud”? Maybe you’ve seen it mentioned in your projects, or maybe you’re just curious about what all the fuss is about. Well, buckle up, because we’re diving deep into the world of sovereign cloud and why it’s becoming increasingly important …