AWS WAF (Web Application Firewall) and Shield provide protection against web exploits and DDoS attacks. This guide covers implementing comprehensive web application security using AWS native services to protect your applications from common threats. Web application security requires multiple layers of protection including WAF rules, rate limiting, bot management, and …
Helm Chart Security: Securing Kubernetes Package Management
Helm is the de facto package manager for Kubernetes, but Helm charts can introduce security vulnerabilities if not properly vetted and configured. This guide covers securing Helm deployments from chart development to production deployment. Helm chart security encompasses chart provenance, secure defaults, secrets management, and runtime security configurations. Understanding these …
Ansible Security Automation: Infrastructure Hardening at Scale
Ansible enables security automation at scale, allowing teams to implement consistent security configurations across thousands of servers. From OS hardening to compliance enforcement, Ansible playbooks codify security best practices and ensure they are applied uniformly. Security automation with Ansible reduces human error, ensures consistency, and enables rapid response to vulnerabilities. …
AWS CloudTrail and Security Monitoring: Comprehensive Audit Guide
AWS CloudTrail provides comprehensive logging of API calls and events across your AWS infrastructure. Combined with CloudWatch, EventBridge, and Security Hub, it forms the foundation of AWS security monitoring. This guide covers implementing effective audit logging and threat detection. Effective security monitoring requires collecting the right data, storing it securely, …
CI/CD Pipeline Security: Protecting Your Software Delivery Process
CI/CD pipelines are critical infrastructure that build, test, and deploy your applications. A compromised pipeline can inject malicious code into production, steal secrets, or provide attackers with persistent access to your systems. This guide covers comprehensive security practices for protecting your software delivery process. Pipeline security encompasses access control, secrets …
Docker Security Best Practices: Building Secure Container Images
Docker containers have revolutionized application deployment, but they introduce unique security challenges. Building secure container images requires attention to base image selection, dependency management, and runtime configuration. This guide covers comprehensive Docker security practices for production environments. Container security starts with the image build process. A vulnerable base image or …
Amazon EKS Security Hardening: Complete Implementation Guide
Amazon EKS (Elastic Kubernetes Service) provides managed Kubernetes clusters, but security remains a shared responsibility. This comprehensive guide covers hardening EKS clusters from network configuration to pod security, ensuring your containerized workloads are protected against modern threats. EKS security encompasses multiple layers: the control plane managed by AWS, the data …
Terraform State Management and Security: Enterprise Best Practices
Terraform state is the backbone of infrastructure as code, containing sensitive information about your resources. Proper state management is critical for team collaboration, security, and disaster recovery. This guide covers enterprise-grade practices for managing Terraform state securely. The state file contains resource IDs, attributes, and potentially sensitive data like database …
AWS Lambda Security Best Practices: Comprehensive Protection Guide
AWS Lambda has revolutionized how we build and deploy applications, enabling serverless architectures that scale automatically and reduce operational overhead. However, the serverless paradigm introduces unique security challenges that require specialized approaches. This comprehensive guide covers everything you need to know about securing Lambda functions in production environments. While AWS …
Kubernetes Network Policies: Complete Guide to Pod-Level Security
Kubernetes Network Policies provide a powerful mechanism for controlling traffic flow between pods, namespaces, and external endpoints. By default, Kubernetes allows all pod-to-pod communication, which creates significant security risks in multi-tenant environments. Network Policies enable you to implement micro-segmentation and zero-trust networking principles within your cluster. Understanding and implementing Network …
Security Champions Programs and Developer Security Training
Security Champions programs embed security expertise within development teams, creating a scalable approach to security culture. Combined with targeted training, they transform developers into the first line of defense. Security Champion Role Advocate for security within their team Review code for security issues Triage security findings Share knowledge and best …
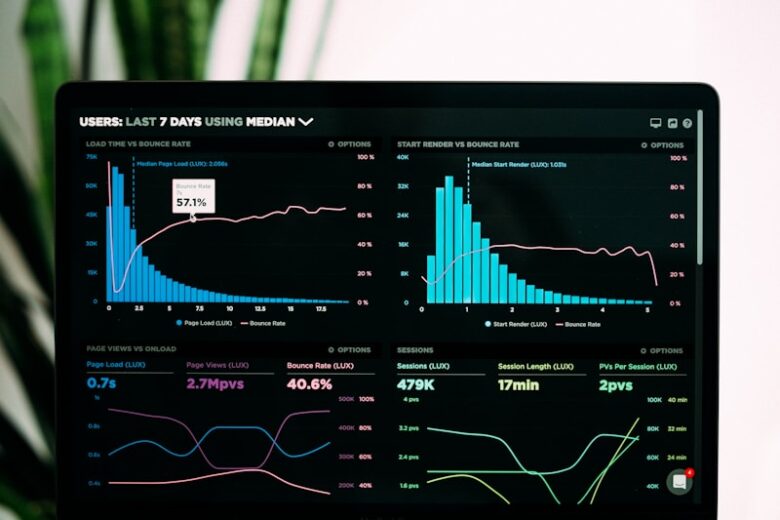
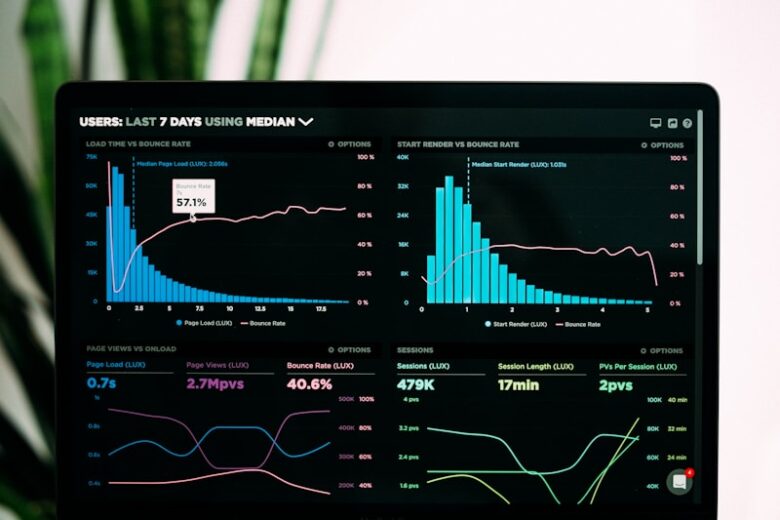
DevOps Metrics: DORA and SPACE Framework Implementation
DORA metrics measure software delivery performance, while SPACE provides a holistic view of developer productivity. Together, they help teams understand and improve their engineering effectiveness. DORA Metrics Deployment Frequency: How often code deploys to production Lead Time for Changes: Time from commit to production Change Failure Rate: Percentage of deployments …