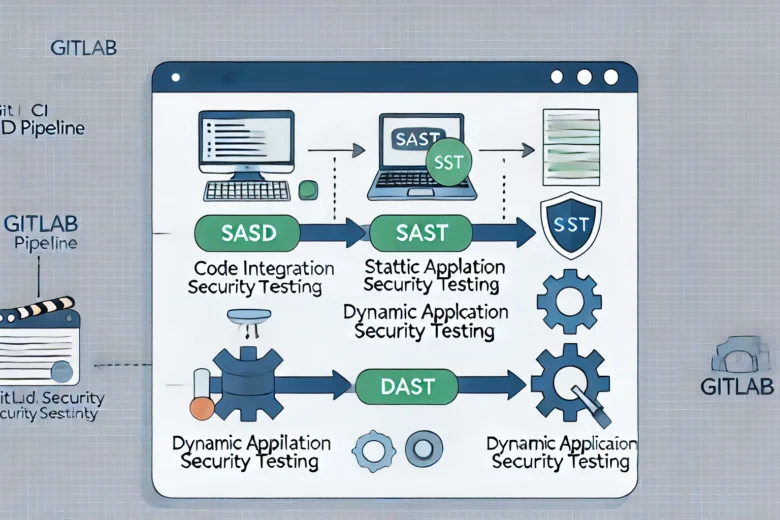
Introduction In today’s fast-moving world of software development, making sure your code is secure is more important than ever. Developers are writing and pushing code fast, but it has to be safe before it goes live. A great way to keep things secure is by using SAST (Static Application Security …
CISSP Certification Guide: Pass the Exam and Advance Your Cybersecurity Career
In today’s rapidly evolving cybersecurity landscape, obtaining the CISSP certification is a significant achievement for IT professionals. The Certified Information Systems Security Professional (CISSP) credential is recognized worldwide and is highly respected among cybersecurity experts. It demonstrates your ability to design, implement, and manage a top-notch cybersecurity program. This guide …
Building Secure AI with MLSecOps: A Comprehensive Guide
Building Secure AI with MLSecOps The rapid growth of artificial intelligence (AI) and machine learning (ML) has transformed many industries, providing powerful capabilities for automation, predictive analytics, and decision-making. However, as these technologies become more widely adopted, ensuring their security and trustworthiness has become a top priority. The concept of …
Accelerate Secure by Design Practices with the Aranya Open-Source Toolkit
The Growing Need for Secure by Design in Software Development In today’s rapidly evolving digital landscape, security threats like malware, ransomware, and AI-driven attacks pose significant risks to organizations. To address these challenges, the concept of secure by design has emerged as a fundamental approach in software development, where security …
How to Self-Host a Container Registry: A Comprehensive Guide
As containerized applications continue to grow in popularity, managing container images efficiently has become critical for development and DevOps teams. Public container registries like Docker Hub, Amazon ECR, and Google Cloud Artifact Registry are common choices, but self-hosting a container registry offers more control, security, and flexibility. Whether you’re an …
Top Cloud Security Certifications: Which one should you choose?
TL;DR: Cloud security is a critical area for modern businesses, and certifications are a great way to prove your skills in this field. In this post, we cover popular cloud security certifications that will help boost your career and prepare you for securing cloud environments. Read on to discover which …
Prowler: An Open-Source Cloud Security Posture Management (CSPM) Tool
TL;DR: Prowler is an open-source security tool that helps monitor and secure AWS cloud environments. Similar to CSPM solutions, Prowler provides visibility, compliance checks, and security best practices by auditing AWS resources. It is a powerful, free option for businesses looking to enhance their cloud security posture. What is Prowler? …
Data Security Posture Management (DSPM): A Comprehensive Guide
TL;DR In today’s digital landscape, securing sensitive data is more critical than ever. With increasing cyber threats and data breaches, organizations must adopt proactive measures to protect their data. Data Security Posture Management (DSPM) is a powerful approach that helps organizations gain full visibility into their data, assess risks, and …
What is CSPM, Why Your Company Should Use It, and How to Choose the Right Solution?
TL;DR: Cloud Security Posture Management (CSPM) helps companies monitor and secure their cloud environments by detecting misconfigurations, ensuring compliance, and automating security fixes. This article explains what CSPM is, why it’s important, and provides a comparison of top CSPM providers like Wiz, Orca Security, and Prisma Cloud to help you …
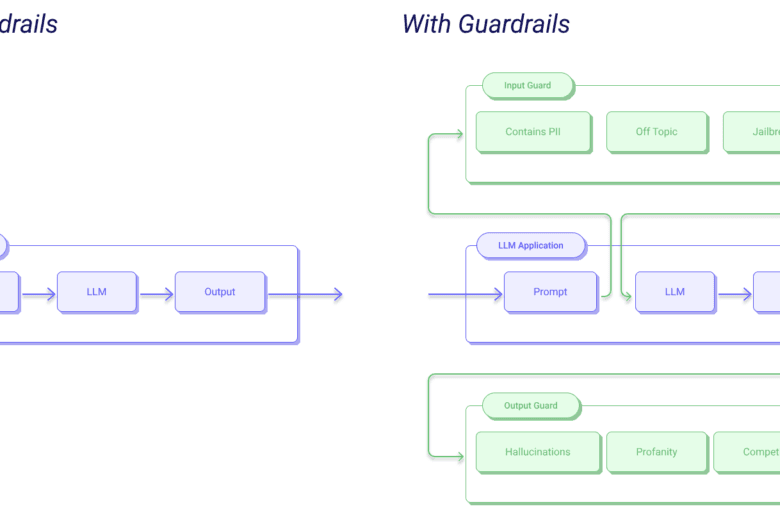
How AI Guardrails improve Security in DevSecOps
TL;DR: DevSecOps is important for secure software development, and using AI guardrails makes security easier. AI platforms like Prime Security help developers find problems early, follow security best practices, and reduce their workload. This blog talks about how AI guardrails are changing DevSecOps, why they are important, and how they …
Getting Started with Cloud Security
TL;DR: Starting with cloud security involves understanding your responsibilities, using strong authentication, encrypting your data, and monitoring your cloud environment. Follow these basic steps to protect your cloud setup from potential security threats. As more businesses move to the cloud, securing their cloud environments becomes a top priority. Cloud security …
Artificial Intelligence Statistics You Need to Know: Who is Using It & How?
TL;DR: Artificial intelligence is revolutionizing every aspect of our lives, from business automation to creative pursuits. In this blog, we compile the latest statistics to give you a snapshot of how AI is being used, who’s using it, and how it’s shaping the world in 2024. AI is Everywhere: The …