TL;DR
GitHub Actions is a powerful tool for automating tasks, like creating AWS resources. Combined with CI/CD (Continuous Integration/Continuous Deployment) and Terraform, it simplifies workflows, saves time, and reduces errors. In this post, you’ll learn how to use GitHub Actions and Terraform to automate the creation of an S3 bucket on AWS.
What is GitHub Actions?
GitHub Actions is a tool built into GitHub that allows developers to automate different parts of the software development process. It helps run scripts and workflows in response to events in your repository. For example, you could use it to test code automatically when changes are made, deploy updates, or even clean up unused resources.
With GitHub Actions, you can create workflows that automate repetitive tasks. These workflows are written in YAML files and define a series of steps that run based on triggers, like when code is pushed or a pull request is opened. You can think of it as a helpful assistant that keeps everything organized and up-to-date without needing manual intervention. GitHub Actions integrates seamlessly with GitHub, making it easy to use for both small and large projects.
GitHub Actions also offers access to many pre-built actions from the GitHub Marketplace. These actions can perform tasks like setting up a programming environment, configuring cloud services, or sending notifications. This flexibility makes GitHub Actions an essential tool for modern software development teams.
What is CI/CD?
CI/CD stands for Continuous Integration and Continuous Deployment. It is a practice in software development that makes releasing software faster and more reliable. Here’s a quick breakdown:
- Continuous Integration (CI): This is the process of automatically testing and integrating new code into the existing codebase. Developers push their code changes to a shared repository, where automated tests run to catch bugs early. CI helps maintain code quality and ensures the application remains stable, even with frequent changes.
- Continuous Deployment (CD): After code passes the tests, it’s automatically deployed to the environment where it’s meant to run, like a server or cloud infrastructure. This ensures that the latest changes are always available to users without manual intervention.
In short, CI/CD helps developers release code more frequently and with fewer errors. GitHub Actions is one of the tools that can be used to implement a CI/CD pipeline, allowing for a streamlined development process and faster delivery of new features.
Creating an AWS S3 Bucket Using GitHub Actions and Terraform
In this example, we will use the creation of an S3 bucket, but we could easily perform more complex tasks, such as creating EC2 instances, load balancers (ALB), ACM configurations, and integration with Route 53.
In this section, we will create an AWS S3 bucket using GitHub Actions and Terraform, demonstrating how CI/CD concepts work to automate tasks. Terraform is an infrastructure-as-code tool that makes managing cloud resources more efficient and consistent.
Step 1: Setting Up GitHub Secrets
To interact with AWS, we need access keys. For security reasons, it’s best to store these keys as GitHub Secrets rather than hardcoding them in the workflow file. Follow these steps:
- Go to your GitHub repository.
- Click on Settings > Secrets and variables > Actions > New repository secret.
- Add two secrets named
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY. These will be used to authenticate with AWS.
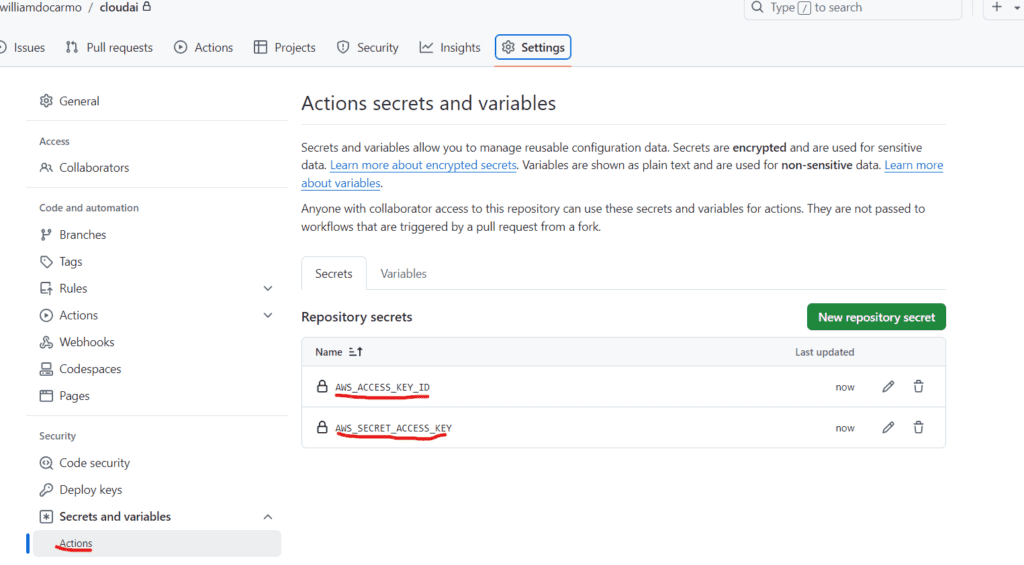
Using secrets ensures that sensitive information is kept secure and isn’t exposed in your code or logs. This is crucial for maintaining security when working with cloud services.
Step 2: Writing the GitHub Actions Workflow
To automate the creation of an S3 bucket, we’ll create a GitHub Actions workflow file called .github/workflows/create-s3-bucket.yml. Here’s the YAML configuration:
name: Terraform Workflow
on:
push:
branches:
- main
workflow_dispatch: # Allows manual execution
inputs:
destroy:
description: 'Run terraform destroy'
required: false
default: 'false'
jobs:
terraform:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v2
with:
aws-access-key-id: '${{ secrets.AWS_ACCESS_KEY_ID }}'
aws-secret-access-key: '${{ secrets.AWS_SECRET_ACCESS_KEY }}'
aws-region: us-east-1
- name: Set up Terraform
uses: hashicorp/setup-terraform@v2
- name: Initialize Terraform
run: terraform init
- name: Plan Terraform changes
run: terraform plan -out=tfplan
- name: Apply Terraform changes if not destroy
if: github.event.inputs.destroy != 'true'
run: terraform apply -auto-approve tfplan
- name: Destroy Terraform infrastructure
if: github.event.inputs.destroy == 'true'
run: terraform destroy -auto-approve
Step 3: Writing the Terraform Configuration
To create the S3 bucket, we need to define a Terraform configuration file. Create a new file called main.tf in your repository:
provider "aws" {
region = "us-east-1"
}
resource "aws_s3_bucket" "github_actions_bucket" {
bucket = "cloudai-my-first-cicd"
}Breaking Down the Workflow
- Trigger (on: push): This workflow runs whenever new code is pushed to the
mainbranch. This ensures that the S3 bucket creation is triggered automatically whenever there are changes, keeping the infrastructure up to date. - Job Definition (jobs): The job runs on an Ubuntu virtual environment (
ubuntu-latest), which provides a consistent environment for running scripts. - Steps:
- Checkout code: Uses the
actions/checkoutaction to pull the latest code from the repository. - Configure AWS credentials: Uses the
aws-actions/configure-aws-credentialsaction to set up AWS authentication using the secrets we defined. This step configures the AWS CLI with the correct keys and region. - Set up Terraform: Uses the
hashicorp/setup-terraformaction to set up Terraform in the workflow environment. - Initialize Terraform: Runs
terraform initto initialize the Terraform working directory. - Apply Terraform configuration: Runs
terraform apply -auto-approveto create the S3 bucket defined in themain.tffile.
Step 4: Pushing Changes to Trigger the Workflow
Once you push changes to the main branch of your repository, the workflow will run automatically. You can check the progress of the workflow under the Actions tab in your GitHub repository. If everything is set up correctly, you should see the job complete successfully and the S3 bucket created in your AWS account.
The Actions tab provides detailed logs for each step of the workflow, making it easy to troubleshoot any issues. This transparency helps developers quickly identify and fix problems, ensuring automation runs smoothly.
Benefits of Using GitHub Actions and Terraform for CI/CD
- Automation: Automates repetitive tasks, freeing up time for developers to focus on more important work. By reducing manual intervention, GitHub Actions and Terraform help teams work more efficiently and reduce the chance of human error.
- Integration: GitHub Actions is tightly integrated with GitHub, making it easy to set up workflows triggered by repository events. Terraform allows for consistent infrastructure management, reducing the risk of configuration drift.
- Scalability: You can add more workflows for various AWS services or other automation needs as your project grows. GitHub Actions and Terraform can be used to automate not only cloud infrastructure but also testing, deployment, and monitoring, making them versatile tools for DevOps.
Best Practices for Using GitHub Actions, Terraform, and CI/CD
- Keep Secrets Secure: Always use GitHub Secrets to store sensitive information like access keys and tokens. This prevents unauthorized access to your cloud resources.
- Use Environment-Specific Workflows: Consider creating separate workflows for different environments (e.g., development, staging, production). This helps ensure that changes are tested thoroughly before being deployed to production.
- Monitor Workflow Runs: Regularly check the Actions tab to monitor workflow runs and catch any issues early. Setting up notifications for failed runs can help you respond quickly to problems.
- Security Considerations: Limit permissions for AWS credentials used in workflows. Use least-privilege principles to minimize risks when automating cloud infrastructure tasks.
Conclusion
GitHub Actions is a powerful tool for automating DevOps tasks, and when combined with Terraform and CI/CD, it can significantly enhance your development workflows. By setting up a simple workflow, you can automate AWS operations like creating an S3 bucket, reducing manual tasks and potential human errors. With GitHub Actions and Terraform, you can create scalable and reliable CI/CD pipelines, making your software development process faster and more efficient.
Whether you’re just starting with DevOps or looking to streamline your existing processes, GitHub Actions and Terraform provide accessible and flexible ways to automate workflows. The ability to define custom workflows, integrate with cloud services, and leverage pre-built actions makes them must-have tools for modern software development teams.
Ready to Take Action?
Have you used GitHub Actions for any automation projects? What challenges did you face? Try setting up your first GitHub Actions workflow today and experience the power of automation firsthand! Explore more possibilities by creating additional workflows to automate other parts of your development and deployment processes, and watch as your efficiency skyrockets.

