Cybersecurity threats are constantly changing, and attacks that target systems to make them unavailable are becoming more common. Some of the most common attacks are Denial of Service (DoS), Distributed Denial of Service (DDoS), Distributed Reflective Denial of Service (DRDDoS), and Ping of Death (PoD) attacks. Each of these attacks works in a different way to disrupt services, and understanding their differences can help protect against them. This article will explain each attack type, how they work, and how to defend against them.
Denial of Service (DoS) Attack
A Denial of Service (DoS) attack is one of the simplest types of cyberattacks. It is designed to make a system, server, or network unavailable for regular users. In a DoS attack, a single attacker floods the target with a lot of traffic or sends bad requests to use up system resources like CPU, memory, or bandwidth. This makes it impossible for regular users to access the system.
DoS attacks are relatively easy to perform compared to other attacks, and attackers often use simple tools that can send repetitive requests automatically. An example of a DoS attack is sending too many ICMP (Internet Control Message Protocol) requests to a server, which makes the server too busy to respond to normal users. The effect of a DoS attack can range from being a small annoyance to causing major disruptions, depending on how powerful the attack is and how strong the target system is.
DoS attacks are usually easier to detect and stop since they come from a single source. However, they can still be disruptive, especially for smaller organizations that don’t have a lot of resources for defense.
Distributed Denial of Service (DDoS) Attack
A Distributed Denial of Service (DDoS) attack is a more advanced and powerful type of DoS attack. In a DDoS attack, the attacker uses multiple devices that have been compromised, often called a botnet, to attack a system or network. These devices can be spread all over the world, making it harder to stop the attack or figure out where it is coming from.
Because DDoS attacks use many devices, they are much harder to defend against than regular DoS attacks. A DDoS attack sends a large amount of traffic from many devices to overwhelm even well-protected systems. Common types of DDoS attacks include HTTP Flood, UDP Flood, and SYN Flood attacks, each of which takes advantage of different parts of a system. For example, an HTTP Flood sends a large number of web requests to a server, making it too busy to handle real users.
DDoS attacks are very dangerous because they can involve thousands or even millions of devices, making it challenging to block the attack without also affecting real users. These attacks can disrupt big websites, financial institutions, and government services, leading to significant financial and reputational damage.
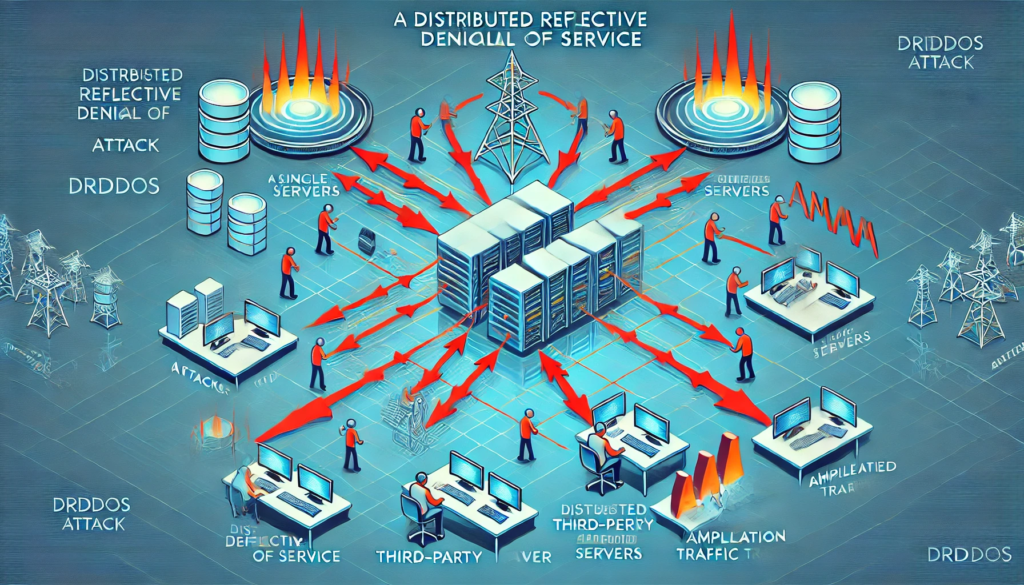
Distributed Reflective Denial of Service (DRDDoS) Attack
A Distributed Reflective Denial of Service (DRDDoS) attack, also called a reflection attack, is a type of DDoS attack that uses third-party servers to amplify the attack. In a DRDDoS attack, the attacker pretends to be the victim by spoofing their IP address and sends requests to other servers. These servers, thinking they are responding to a legitimate user, send their responses to the victim’s IP address, overwhelming the target.
A DRDDoS attack works by reflecting and amplifying the attack traffic using third-party servers. Servers like DNS and NTP are often used because they can send back a much larger response compared to the original request. This allows attackers to cause a lot of damage with little effort. For example, a DNS reflection attack uses a small request to create a much larger response, making the attack more powerful.
DRDDoS attacks are difficult to defend against because the traffic appears to come from legitimate servers, making it hard to tell what is malicious and what is normal. The use of amplification also makes the attack much more effective, as a small effort by the attacker can result in a large amount of harmful traffic.
Ping of Death (PoD) Attack
The Ping of Death (PoD) is an older type of DoS attack that takes advantage of how devices handle ICMP packets. In a PoD attack, the attacker sends a large or malformed ping packet to the target. When the target tries to put the packet back together, it can cause a buffer overflow, which can make the system crash, reboot, or become unstable.
PoD attacks were common in the late 1990s and early 2000s, but most modern systems are now protected against them. However, it is still important to understand PoD attacks because they show how bad data can be used to damage systems. Even though PoD attacks are not as common today, similar vulnerabilities can still exist in outdated or misconfigured systems.
Key Differences Between the Attacks
- Source of Attack:
- DoS: A single source is used to attack the target.
- DDoS: Multiple sources (often a botnet) are used to send overwhelming traffic.
- DRDDoS: Third-party servers are used to reflect and amplify the attack.
- PoD: A single source sends oversized or malformed packets to exploit weaknesses.
- Complexity:
- DoS: Simple to carry out and defend against.
- DDoS: More complex due to using multiple devices.
- DRDDoS: More complicated because of reflection and amplification.
- PoD: Simple but effective, though most modern systems are protected.
- Impact:
- DoS: Makes a system or network unavailable by using up resources.
- DDoS: Can severely disrupt large networks, harder to mitigate.
- DRDDoS: Amplifies attack impact through third-party servers.
- PoD: Can crash or reboot systems if they are vulnerable.
- Defense Complexity:
- DoS: Easier to detect and block since it comes from a single source.
- DDoS: Requires advanced techniques like filtering and botnet mitigation.
- DRDDoS: Harder to defend because it uses legitimate servers.
- PoD: Mainly defended by patching systems to avoid vulnerabilities.
Defending Against These Attacks
- Monitoring and Detection: Continuously monitor network traffic to detect unusual activity that might indicate an attack. Use tools like intrusion detection systems (IDS) to identify threats early. Spotting sudden spikes in traffic can help identify an attack in progress.
- Rate Limiting: Rate limiting can help control the number of requests your system can handle at one time, which can prevent DoS attacks from overwhelming your server. It limits how many requests are allowed in a specific period.
- Firewalls and Filtering: Use firewalls to block suspicious IP addresses, and use packet filtering to stop malformed packets from entering your network. Firewalls can help monitor traffic and block unusual requests that could be part of an attack.
- Load Balancers: Load balancers help spread incoming traffic across multiple servers, making it harder for DDoS attacks to bring down your system. They make sure that no single server becomes overwhelmed.
- Anti-DDoS Services: Services like Cloudflare and AWS Shield can help protect against DDoS and DRDDoS attacks by filtering out malicious traffic before it reaches your system. These services use smart algorithms to tell the difference between good and bad traffic.
- Patch Management: Keep your systems and applications updated to close known security gaps. Regular updates help protect against vulnerabilities like PoD attacks, making sure attackers can’t use known exploits.
- Network Redundancy and Anycast Routing: Network redundancy and using anycast routing can help spread traffic across multiple nodes, which can reduce the impact of an attack. Anycast sends traffic to multiple locations, making it harder for attackers to overwhelm a single target.
- Botnet Detection and Mitigation: Since DDoS and DRDDoS attacks often use botnets, tools that detect and block botnet traffic are essential. These tools help identify compromised devices and stop them from joining in an attack.
Conclusion
Understanding the differences between DoS, DDoS, DRDDoS, and PoD attacks is important for defending against them. Each type of attack targets system availability in a different way, and their impacts can be very different. DoS attacks are easier to handle, while DDoS and DRDDoS are more challenging due to their use of multiple devices. PoD attacks, although not as common today, remind us of the importance of keeping systems updated.
By monitoring your systems, using security tools, following best practices, and staying informed about new threats, you can reduce the risk of these attacks and keep your services running smoothly. Being prepared and having strong defenses in place is key to protecting your systems and maintaining user trust.