Vibe coding is revolutionizing how developers build software. Popularized by Andrej Karpathy in early 2025, this AI-assisted development approach shifts your role from writing every line of code to directing outcomes. You express intent in natural language, the AI drafts the implementation, and you steer the edits until the code …
Security Metrics and KPIs for Cloud Environments
This guide provides comprehensive coverage of security best practices for cloud and container environments. Implementing these controls helps protect your infrastructure from threats while maintaining operational efficiency. Modern security requires a proactive approach that integrates security into every aspect of your infrastructure and development processes. This guide covers practical implementation …
DevSecOps Culture and Implementation
This guide provides comprehensive coverage of security best practices for cloud and container environments. Implementing these controls helps protect your infrastructure from threats while maintaining operational efficiency. Modern security requires a proactive approach that integrates security into every aspect of your infrastructure and development processes. This guide covers practical implementation …
Vulnerability Management Program Implementation
This guide provides comprehensive coverage of security best practices for cloud and container environments. Implementing these controls helps protect your infrastructure from threats while maintaining operational efficiency. Modern security requires a proactive approach that integrates security into every aspect of your infrastructure and development processes. This guide covers practical implementation …
Logging Best Practices for Security Operations
This guide provides comprehensive coverage of security best practices for cloud and container environments. Implementing these controls helps protect your infrastructure from threats while maintaining operational efficiency. Modern security requires a proactive approach that integrates security into every aspect of your infrastructure and development processes. This guide covers practical implementation …
Threat Modeling for Cloud Applications
This comprehensive guide covers essential security practices for modern cloud environments. Understanding and implementing these controls is critical for protecting your infrastructure and maintaining compliance with security standards. Security in the cloud requires a different approach than traditional on-premises environments. The shared responsibility model means you must understand what you …
OAuth 2.0 and OIDC Security Implementation
This comprehensive guide covers essential security practices for modern cloud environments. Understanding and implementing these controls is critical for protecting your infrastructure and maintaining compliance with security standards. Security in the cloud requires a different approach than traditional on-premises environments. The shared responsibility model means you must understand what you …
Vault Transit Secrets Engine: Encryption as a Service
This comprehensive guide covers essential security practices for modern cloud environments. Understanding and implementing these controls is critical for protecting your infrastructure and maintaining compliance with security standards. Security in the cloud requires a different approach than traditional on-premises environments. The shared responsibility model means you must understand what you …
CI/CD Pipeline Security: Protecting Your Software Delivery Process
CI/CD pipelines are critical infrastructure that build, test, and deploy your applications. A compromised pipeline can inject malicious code into production, steal secrets, or provide attackers with persistent access to your systems. This guide covers comprehensive security practices for protecting your software delivery process. Pipeline security encompasses access control, secrets …
Security Champions Programs and Developer Security Training
Security Champions programs embed security expertise within development teams, creating a scalable approach to security culture. Combined with targeted training, they transform developers into the first line of defense. Security Champion Role Advocate for security within their team Review code for security issues Triage security findings Share knowledge and best …
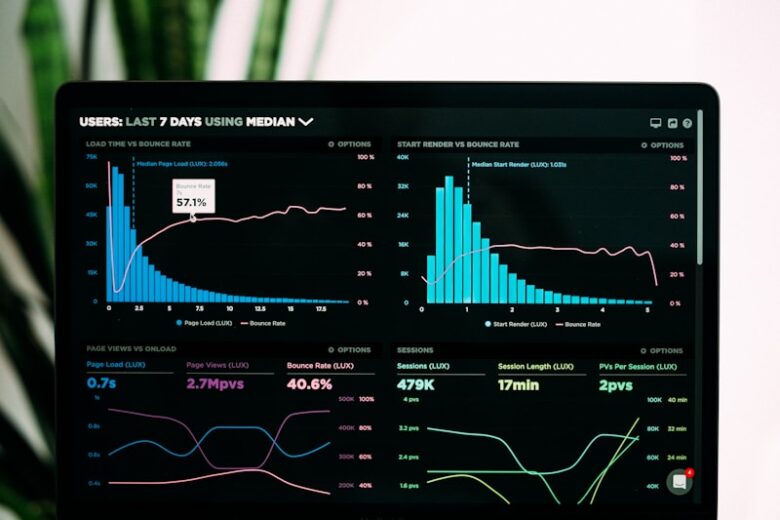
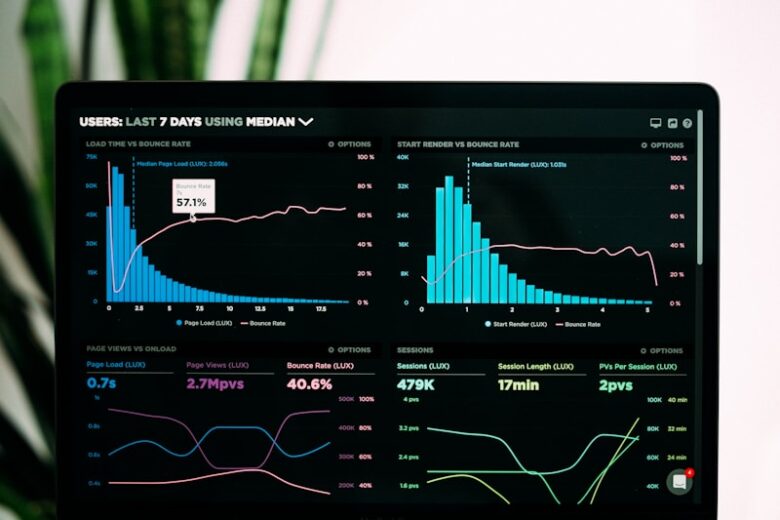
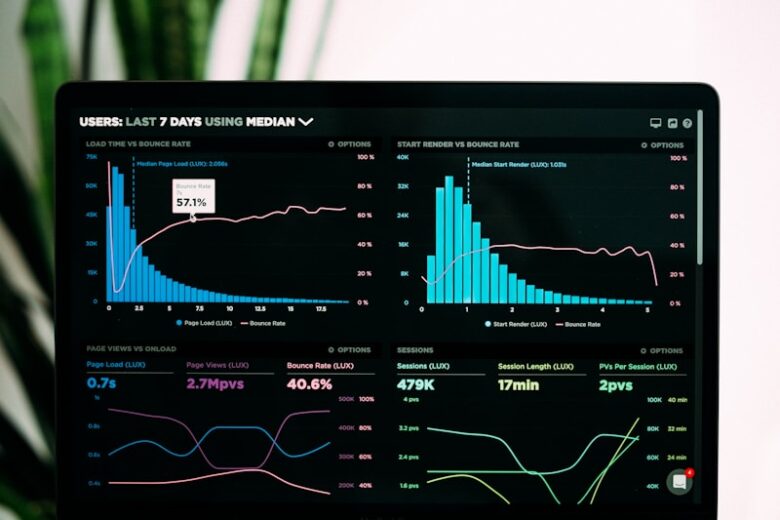
DevOps Metrics: DORA and SPACE Framework Implementation
DORA metrics measure software delivery performance, while SPACE provides a holistic view of developer productivity. Together, they help teams understand and improve their engineering effectiveness. DORA Metrics Deployment Frequency: How often code deploys to production Lead Time for Changes: Time from commit to production Change Failure Rate: Percentage of deployments …
Artifact Registry Security and Dependency Scanning
Artifact registries store build artifacts, container images, and packages. Securing these registries and scanning dependencies prevents supply chain attacks and ensures only trusted artifacts reach production. Private Registry Setup Dependency Scanning JFrog Xray Integration Implement vulnerability policies that block deployment of artifacts with critical vulnerabilities.